-

QR Codes and qrDecoder
Quick Response (QR) codes are two-dimensional barcodes that can store a variety of data, such as alphanumeric text, URLs, or other binary data. They were initially created by Denso Wave, a subsidiary of Toyota, in 1994 for tracking automotive parts during manufacturing. QR codes have gained widespread popularity due to their ability to store large…
-
Serial to Parallel Updates
If you’re an old BASH head like I am, you’ve probably leaned on a FOR loop countless times. It’s become natural enough over the years to just whip one up on the command line, and I use it in scripting every day. Dear Bash FOR loop, You have indeed been trusty and true for many…
-

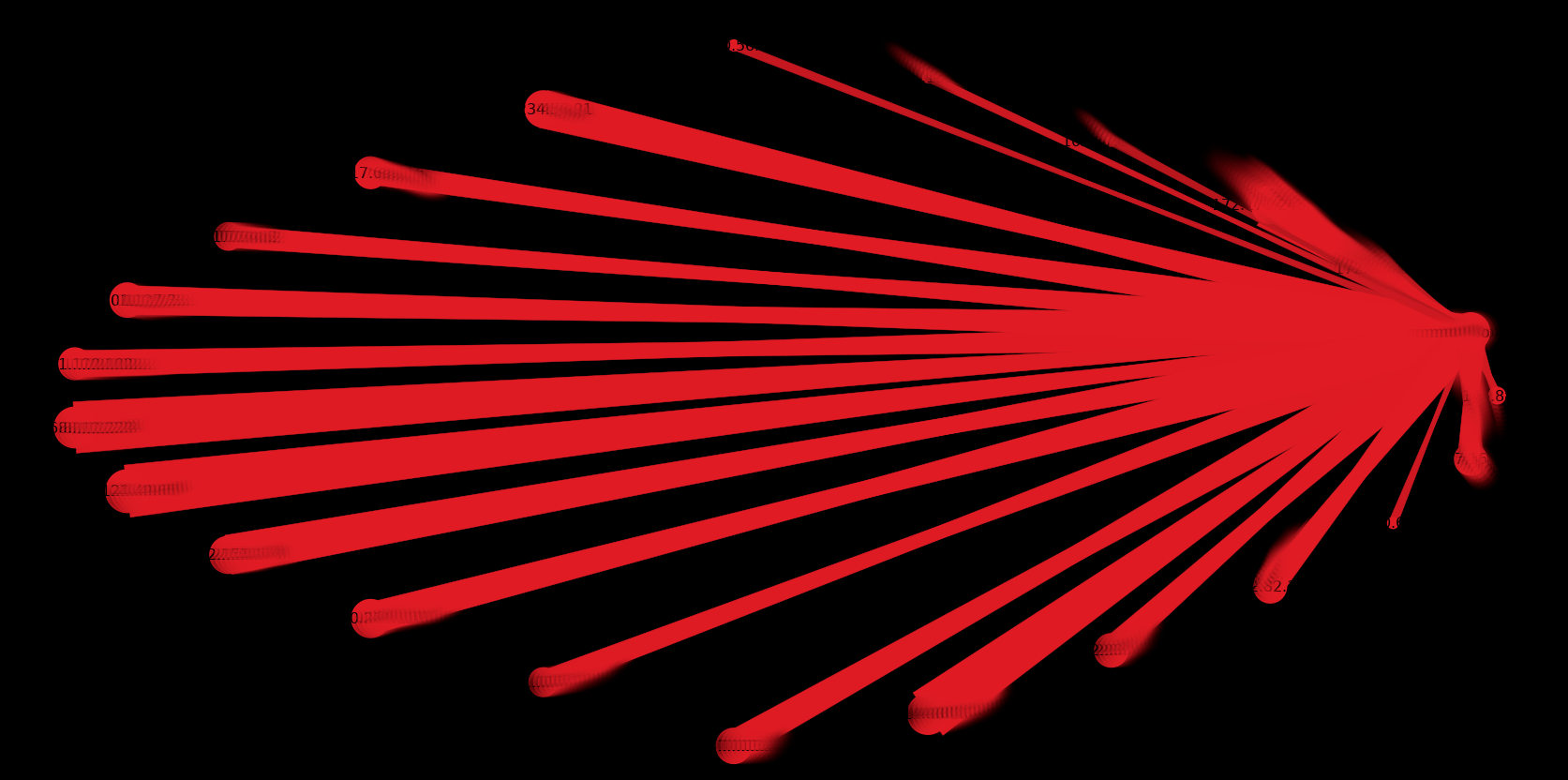
OAUTH Scans Rising
I’ve been monitoring a rise in OAUTH vulnerability scans. Here’s one that hit one of my sensors in Israel between 2023-12-26 16:51:52 and 2023-12-26 16:53:01. Sensor: Israel Source IP: 85.206.173.215 The URL /openam/oauth2/..;/ccversion/Version is associated with a pre-auth remote code execution (RCE) vulnerability in ForgeRock identity and access management software 1. This vulnerability, identified as…
-

Closing out 2023
2023 was an absolute rollercoaster for me on so many levels.I’m not too humble to pat myself on the back because I’m extremely proud of overcoming _every_ obstacle that presented itself as a roadblock on this journey. You can do this too! In the course of the year, I’ve completed six new certifications. Let’s forge…
-

SEC Cyber 8-K Rules Now Effective
The U.S. Securities and Exchange Commission’s (“SEC”) new Form 8-K rules for reporting material cybersecurity incidents took effect on December 18, for filers other than smaller reporting companies. Publicly owned companies operating in the U.S. must comply with a new set of rules requiring them to disclose “material” cyber incidents within 96 hours.Why should the…
-

Terrapin Attack – What You Should Know
Named Terrapin, the new attack works when an attacker obtains an active adversary-in-the-middle position between a ssh client and server. The exploit allows the attacker to assume the identity of both parties, allowing interception and alteration of communications. There are a host of resources available on the Internet for a “deeper dive” into this issue.…
-

Think about building a “Go Bag”.
When the phone rings it’s important to have anticipated anything you may need and have it on hand – especially if you’re walking into an airgap. Here are a few I recently obtained that are performing exceptionally well for me. It’s also a good idea to have more than one, based on functional need. I…
-

Uptick in Scams, Because “Holidays”
As a security practitioner, I receive perhaps more than my fair share of nefarious email. With “Black Friday” and the impending consumer rush I’ve seen an uptick in the behavior. YOU WILL LIKELY SEE A SUBSTANTIAL INCREASE BETWEEN NOW AND JANUARY 5, 2024. Here we have a pair of fairly classic “scam” emails. Both include…
-

Insanely Busy
I’ve been insanely busy as of late. Between school, research, and analysis I’ve kept my plate fairly fully. The volume of data that I’m chewing through is increasing with regularity as well. One of the projects I’ve been working on in my spare cycles is called DShield Manager. It provides some automation in both deployment…
-

Windows 11 Backup Strategy
Microsoft Windows 11 and Solid State storage solutions make it quite a bit easier to perform image-level backups of your computer. An image-level backup is a “kitchen sink, get everything” backup intended to allow you to restore your computer to the operating state it was in from a single image.
-

Using “Find My” to locate an Apple AirTag with extreme accuracy
Using “Find My” to locate an Apple AirTag with extreme accuracy.
-

Cognitive Passwords – What Are They?
Another really simple analogy for these cognitive passwords is the classic “Safe Word”. Settle down now, I’m talking about that conversation you have with your children when they reach an appropriate age, wherein you agree upon a safe word or phrase that any stranger the child has never met must repeat if they are to…



