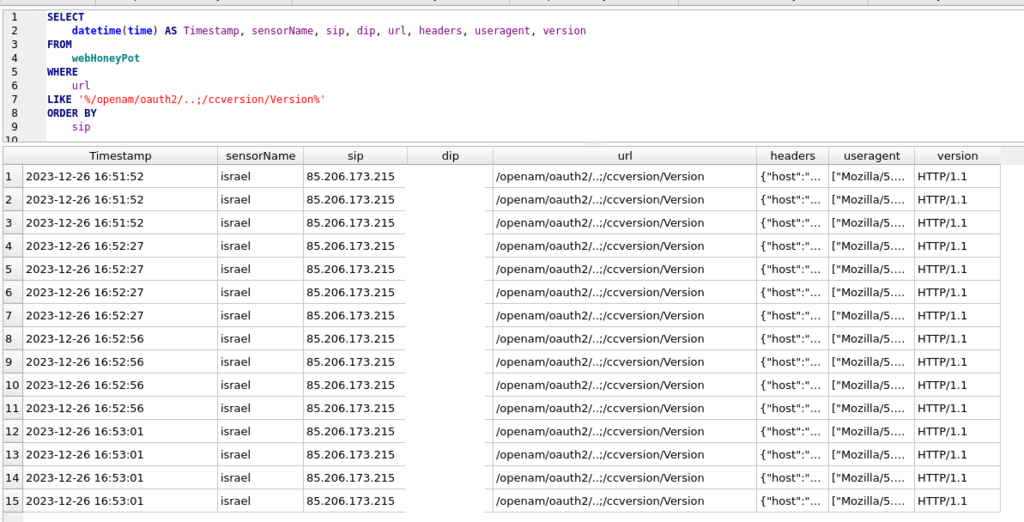
I’ve been monitoring a rise in OAUTH vulnerability scans. Here’s one that hit one of my sensors in Israel between 2023-12-26 16:51:52 and 2023-12-26 16:53:01.
Sensor: Israel
Source IP: 85.206.173.215
The URL /openam/oauth2/..;/ccversion/Version is associated with a pre-auth remote code execution (RCE) vulnerability in ForgeRock identity and access management software 1. This vulnerability, identified as CVE-2021-35464, allows attackers to execute arbitrary code on the affected system by exploiting unsafe object deserialization via the ccversion endpoint 1 2. The vulnerability exists in ForgeRock Access Manager versions below 7.0 running on Java 8 and also in unpatched versions of the Open Identify Platform’s fork of OpenAM 1.
The vulnerability can be exploited by sending a single request to the ccversion endpoint with a serialized object 1. The following is an example of a proof-of-concept exploit:
GET /openam/oauth2/..;/ccversion/Version?jato.pageSession=<serialized_object>
ForgeRock has issued a security advisory to provide information on this vulnerability and will be updating it if and when patches are available 1. In the meantime, organizations running ForgeRock Access Manager versions below 7.0 or using the latest release of the Open Identify Platform’s fork of OpenAM are urged to prioritize upgrading or applying the mitigations within an accelerated patch window if possible, and at the very least within the 30-day window if you are following the typical 30-60-90 day patch criticality cadence 1.
Source(s)
1. ForgeRock Access Manager/OpenAM Pre-Auth Remote Code Execution … – Rapid7
2. Pre-auth RCE in ForgeRock OpenAM (CVE-2021-35464)
3. OpenAM 13 > Release Notes – ForgeRock


