Named Terrapin, the new attack works when an attacker obtains an active adversary-in-the-middle position between a ssh client and server. The exploit allows the attacker to assume the identity of both parties, allowing interception and alteration of communications.
There are a host of resources available on the Internet for a “deeper dive” into this issue. In this post I’m parroting researchers from Germany’s Ruhr University Bochum who have provided a Scanner for evaluating systems. Their publication is available at: https://terrapin-attack.com.
Do we need to panic?
Afterall, this is precisely the kind of activity (man-in-the-middle) that SSH was invented to prevent, right? Not really. There are some gymnastics involved in achieving a successful MITM position. All the same we’re going to see publications in the trades and click-baits that might infer that the sky is suddenly falling. It’s not. The larger threat to encrypted communications, and encryption as a whole moving forward, will be quantum computing.
For the paranoid (me included) mitigation is exceptionally simple. Update the SSH packages for my chosen distribution of Linux. What about my Windows hosts? It’s unknown at this time if this will be “the thing” that urges Microsoft to update their own woefully outdated distributions and publish them for consumption via WSUS. If your current deployments of SSH in a Windows environment aren’t derived from very recent source/binary official releases on github shift to this methodology as quickly as you can.

Performing a scan against a local WSL2 instance of Ubuntu reveals the system is vulnerable to the attack.
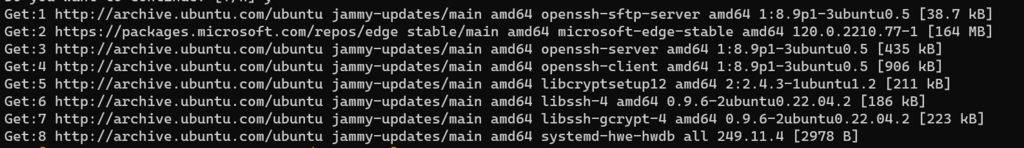
Updates available via apt for Ubuntu are already available.
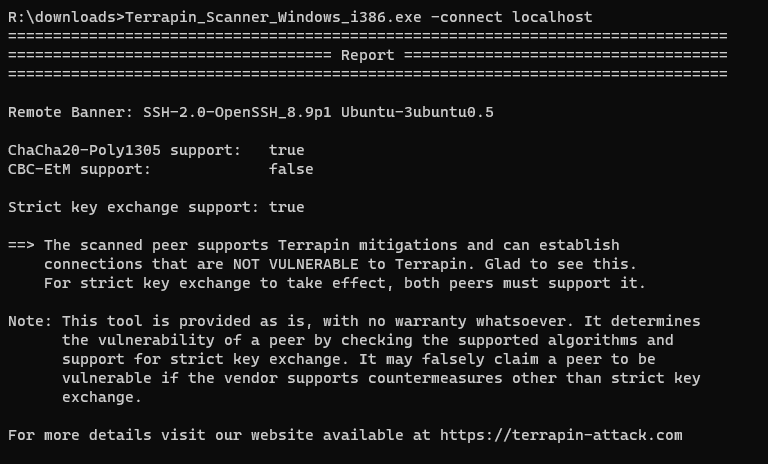
Subsequent scan of the system reports no longer vulnerable.
Need help figuring out how to secure SSH in your Windows environment?
I highly recommend Jason Fossen’s SEC505: Securing Windows and PowerShell Automation


