-
Location, Location, Location.
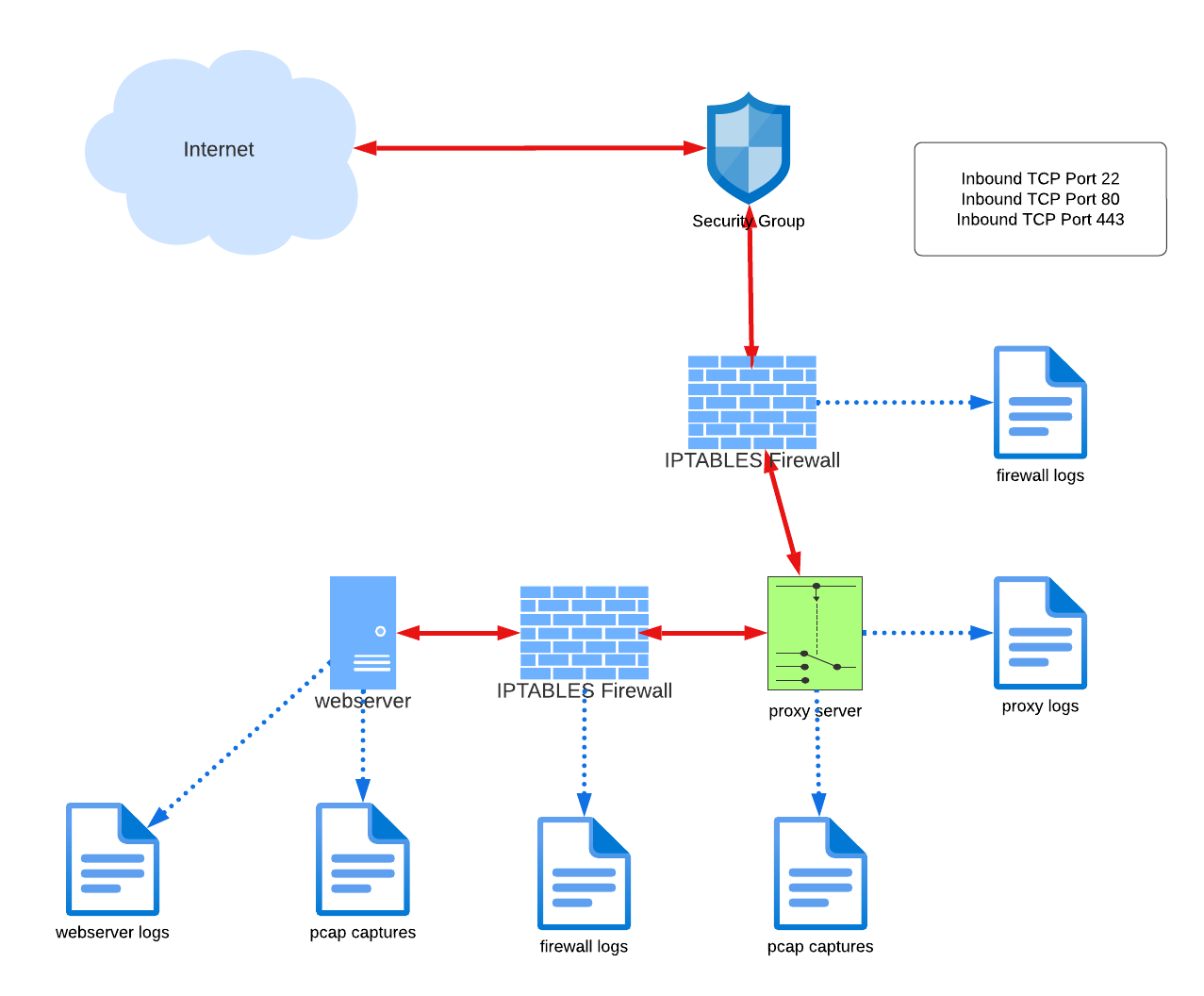
In the real estate business, it’s often said the three most important things are location, location, and location. The same can be said for where security practitioners opt to capture network packets for analysis. Today I’ll quickly examine the difference between a pair of deployments along with their strengths and weaknesses. I’m using a “import…
-

AWS Terraform Template
You want to get started in AWS and you want to learn how to do it with Terraform. You’ve read countless how-to articles, perhaps a book or two, and even watched some YouTube… and you still don’t feel like you “get it”. Or worse, you think you get it, but your code isn’t working. It’s…
-

Haystacks and Needles: Digging for Interest
While an intern with the ISC as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program, I performed a substantial amount of research and analysis on the daily. While most students install a honeypot locally on a Raspberry Pi to gather attack information, I took extra steps to deploy a personal global network of…
-

Migrating Virtual Machine VMware to Proxmox
With the recent announcement that VMware ESXi will no longer be made available for home users for free, many in the industry are turning to Proxmox for their virtual needs. Below find instructions I hastily cobbled together migrating a workstation today.
-

Two-Person Integrity
The two-person rule is a control mechanism designed to achieve a high level of security for especially critical material or operations. Under this rule, access and actions require the presence of two or more authorized people at all times. My first experience with TPI was as a Quartermaster in the United States Navy in the 90’s. The Figure…
-

Spyware in the Crosshairs?
The State Department is implementing a new policy today that will allow the imposition of visa restrictions on individuals involved in the misuse of commercial spyware. This new policy is the most recent action in the United States’ comprehensive approach to countering the misuse of commercial spyware. The governments of Australia, Canada, Costa Rica, Denmark,…
-

Cloudflare Penetration
For me, the story began back on November 2nd, 2023. For the better part of twelve hours, I either couldn’t login at all, or received errors when attempting to manage DNS records. I even opined:“Authentication Error: Code 10000”Please tell me this ain’t some Okta or similar sh*t. (https://twitter.com/TheDustinDecker/status/1720087581575217338) “The company says that this breach did…
-
Consumer Security Cameras
Know what you’re purchasing! Everyone is selling a flavor. The decision to add wireless security cameras to your home or business property is a wise one. The peace of mind associated with knowing a record of “what really happened” is available when necessary is a huge component of the value proposition most Americans base their…
-

Breaking into Cybersecurity
Breaking in to the Cybersecurity industry can be difficult, but certainly not impossible.
-
Random Login Failures
A brief look at a very small sampling of failed logins. I’ve used green to highlight IP addresses known to be “OK” – Starlink out of Denver where my own connection terminates. Others are highlighted in dark pink and represent attacks with certainty. The orange highlighter is for other “items of interest”. Namely the use…
-

Apple “Point Releases”
Apple has released significant “point releases” for all its operating systems. Along with new features, we also receive patches for 29 different vulnerabilities. There is a ZERO DAY exploit observed in the wild against the Apple Webkit. These most recent updates are absolutely essential to maintain the security of your devices. How do I update…
-

Backup Migration Plugin for WordPress
Analysis of network traffic for the period alerted on a generic rule: “ET EXPLOIT file_put_contents php base64 encoded Remote Code Execution 2.” The specific URL requested: http://[redacted].com/wp-content/plugins/backup-backup/includes/backup-heart.php1. The payload is fragmented across six frames and reassembled in hopes of avoiding automated forms of analysis. The vulnerability allows unauthenticated attackers to execute remote code via the…
-

Gitlab Critical Zero-Day
GitLab has released security updates for both the Community and Enterprise Edition to address two critical vulnerabilities, one of them allowing account hijacking with no user interaction. The most critical security issue GitLab patched has the maximum severity score (10 out of 10) and is being tracked as CVE-2023-7028. Successful exploitation does not require any interaction.…