The predominate descriptions for the Tor Project on their website include “Explore Freely” and “Defend yourself against tracking and surveillance. Circumvent censorship.” “Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.”
Tor (The Onion Router) is a free and open-source software that enables anonymous communication over the internet. It was originally developed by the United States Naval Research Laboratory to protect U.S. intelligence communications online1. Tor works by routing internet traffic through a series of servers, or nodes, that are operated by volunteers around the world. Each node in the network only knows the identity of the node that it received data from and the node that it is sending data to, which helps to protect the privacy of users1.
However, the privacy of the Tor network can be compromised in several ways. One of the most common attacks on the network is the use of malicious exit nodes. These are nodes that have been set up specifically to intercept traffic leaving the Tor network. When a user’s traffic is routed through a malicious exit node, the attacker can see all of the user’s unencrypted traffic, including passwords, credit card numbers, and other sensitive information1.
Another way that the privacy of the Tor network can be compromised is through the use of traffic analysis. This involves monitoring the traffic entering and leaving the network to try and identify patterns that can be used to deanonymize users. For example, an attacker might look for patterns in the timing and volume of traffic to try and identify which nodes are being used by a particular user1.
Finally, the privacy of the Tor network can be compromised through the use of browser exploits. These are vulnerabilities in the Tor browser that can be exploited by attackers to gain access to a user’s computer or to bypass the Tor network altogether. For example, an attacker might use a browser exploit to install malware on a user’s computer that can then be used to monitor their activity1.
To mitigate these risks, it is recommended that users of the Tor network take several precautions. These include using the latest version of the Tor browser, avoiding the use of unencrypted protocols like HTTP, and avoiding the use of plugins and other browser extensions that can be used to track users3. Additionally, users should be aware of the risks associated with using the Tor network and should take steps to protect their privacy and security online.
Source(s)
1. Defending Against Malicious Cyber Activity Originating from Tor
2. Is Tor Still Safe to Use? | VPNOverview
3. Tor is under threat from Russian censorship and Sybil attacks
4. NSA and GCHQ target Tor network that protects anonymity of web users …
2008 Called to remind us Tor is NOT anonymous and NOT untraceable.
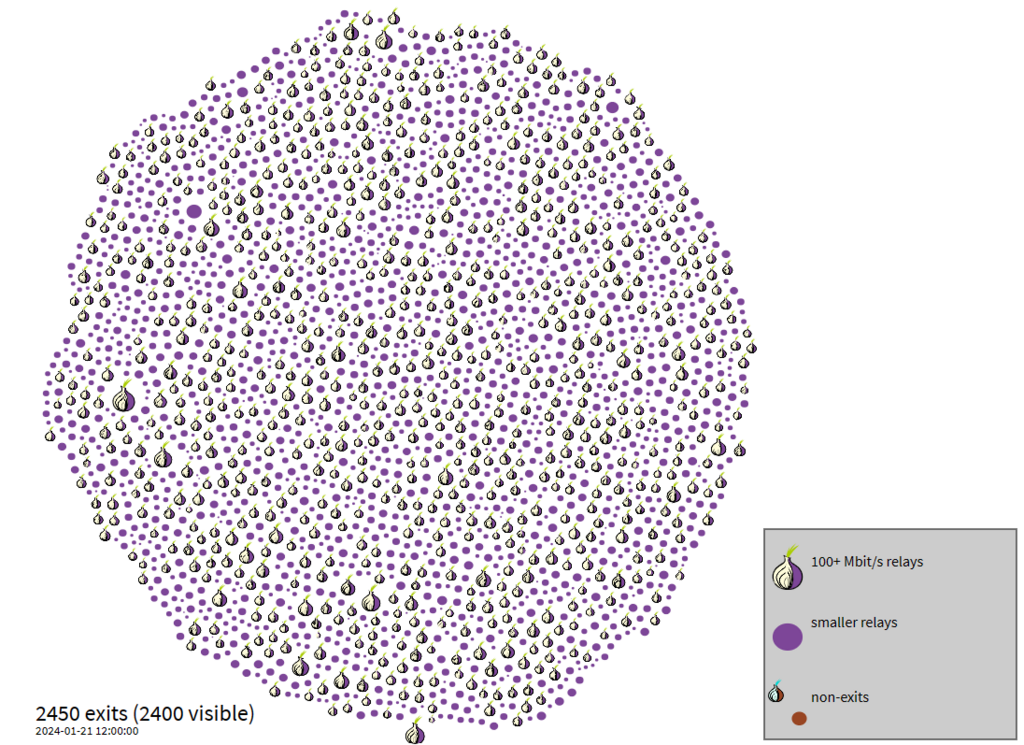
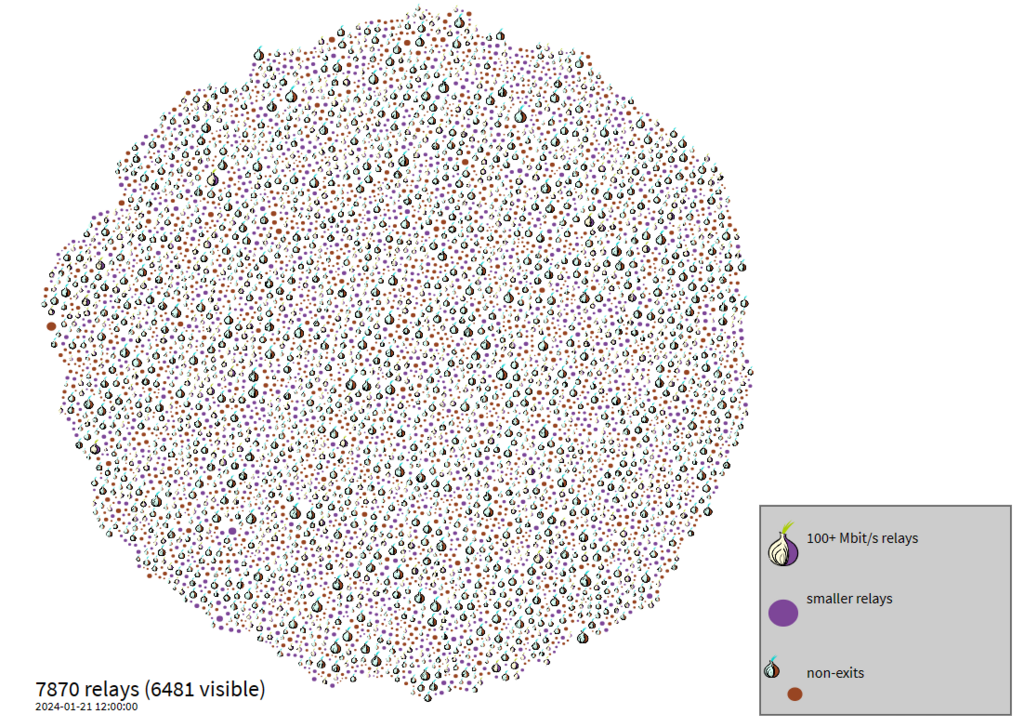
Roughly 2500 “Exit” nodes and just under 8000 “Relay” nodes, are outlined in the images above, provided by the Tor Project. At first glance this may seem large. Big Data, however, would consider this to be a fairly small sample to break apart and analyze.
On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records
https://cdn-resprivacy.pressidium.com/wp-content/uploads/2019/10/cucs-019-13.pdf
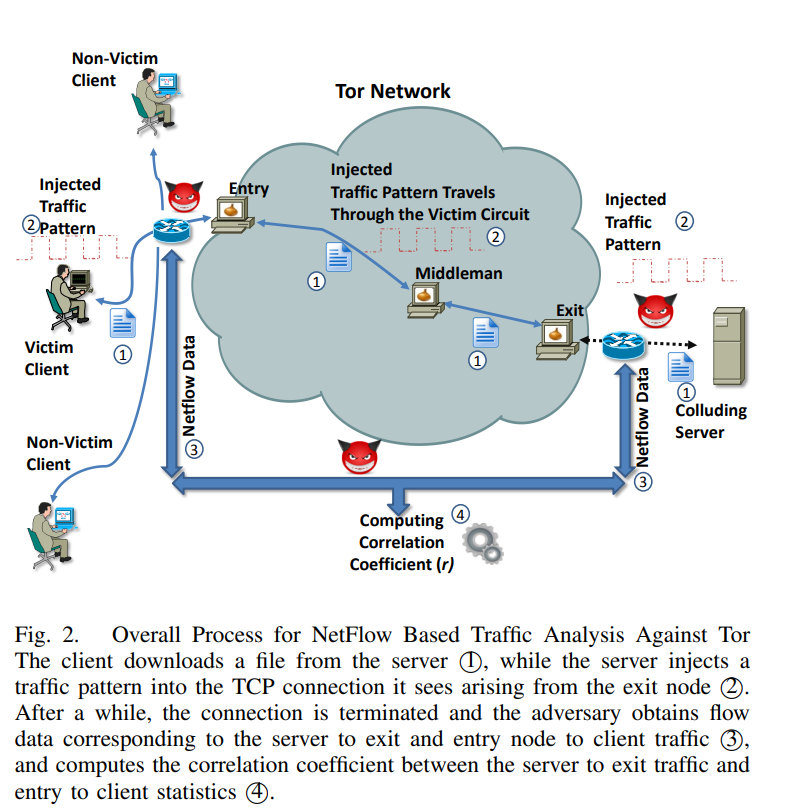
Consider for example this small sampling of alerts on traffic passing one of my monitored systems. Identifying and/or blocking Tor is becoming quite trivial – and as such, so is monitoring.

