-

GIAC GLCD Certification
I’m pleased to share I’ve recently received my GIAC GLCD Certification from SANS! Cloud security involves adapting traditional security practices to the public cloud environment by leveraging the shared responsibility model. It requires applying vendor-provided controls to protect applications, data, and brand within the cloud environment. Effective cloud security includes Identity and Access Management (IAM),…
-

SANS SEC488
I’ve recently started the SANS SEC488 course, which is as intensive as all SANS courses tend to be. In the cloud a solid understanding of Identity and Access Management is crucial from the start; otherwise, there’s a high chance of making early mistakes in design and deployment that can cause significant issues later on. In…
-
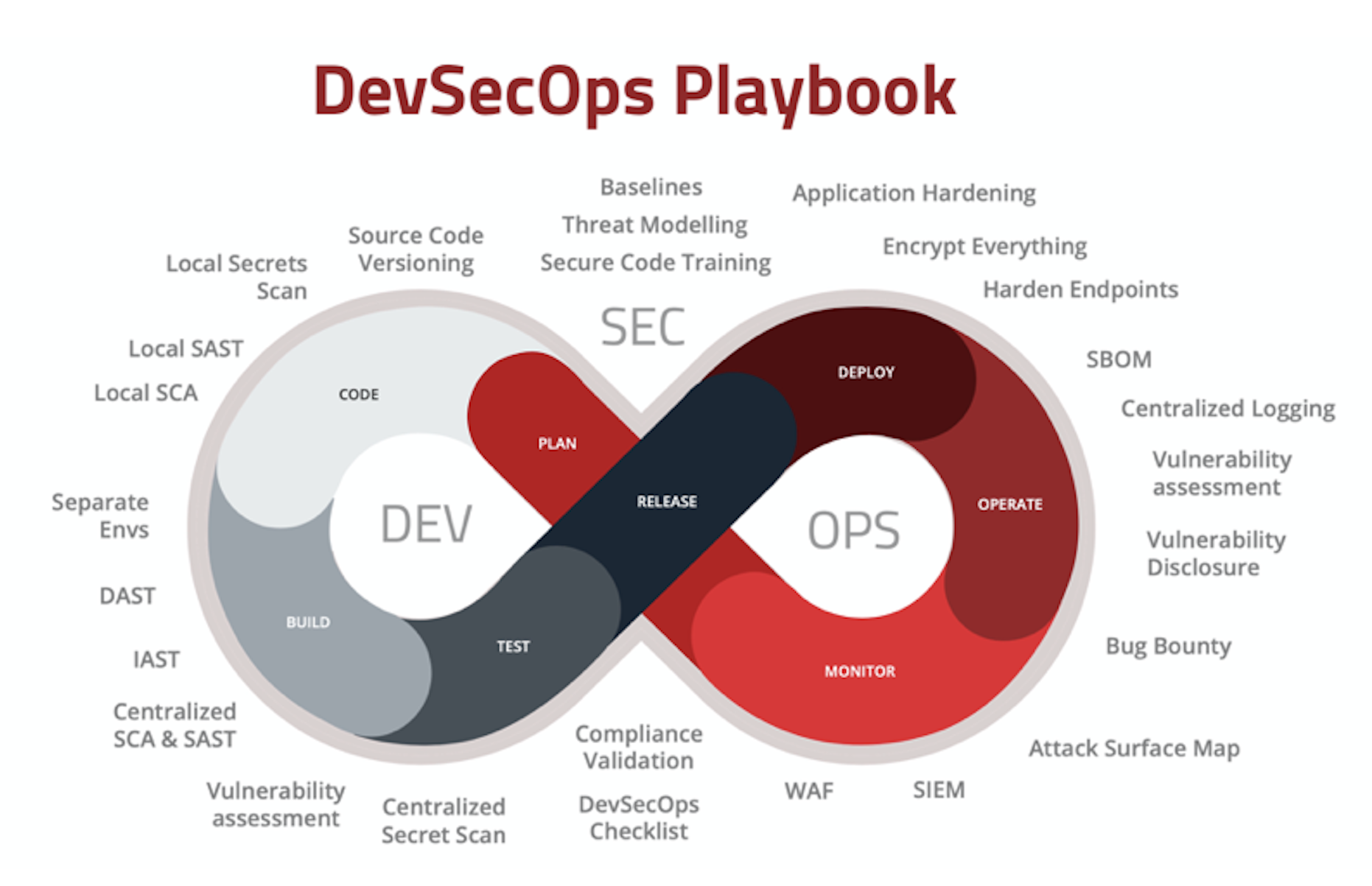
Deep in DevSecOps
I spend a significant portion of my waking hours glued to a laptop coding, reviewing reports, analyzing data and attending school. I’m what the cool kids call “hella busy”. There’s an adage about the cobblers’ children having no shoes, which dovetails nicely with the “eat your own dogfood” principle of DevOps. This is one of…
-

Long time, no updates
It’s been a fair number of minutes since I’ve last posted. I’ve been a fairly busy individual. I had the honor in 2004 of joining the Technology Team at the Burning Man Project! As a WAN Network Engineer at Burning Man, I joined a team responsible for delivering high-capacity network services to support the ongoing…
-

Multi-OS Screen Blanking
The goal: Automate the binary application of daytime/nighttime screen timeout for Windows, macOS and Kali Linux.
-

Little Squeaks
I’d love to say some days are slower than others but it’s not really true. I might spend an enormous amount of time, consuming new skillsets and sharpening my edge. While that’s going on, the Internet will of course continue to Internet. Let’s take a look at a three-day period of alert logging from a…
-

My Little Black Book
A small and perhaps growing, aging or rapidly deprecating Little Black Book of Spells We’ve all done it – consulted the Root of All Knowledge (aka “Google”) and long since forgotten the results. Do you find yourself searching for the same things repeatedly? I sure do. I’ve decided once I’ve done that three or four…
-
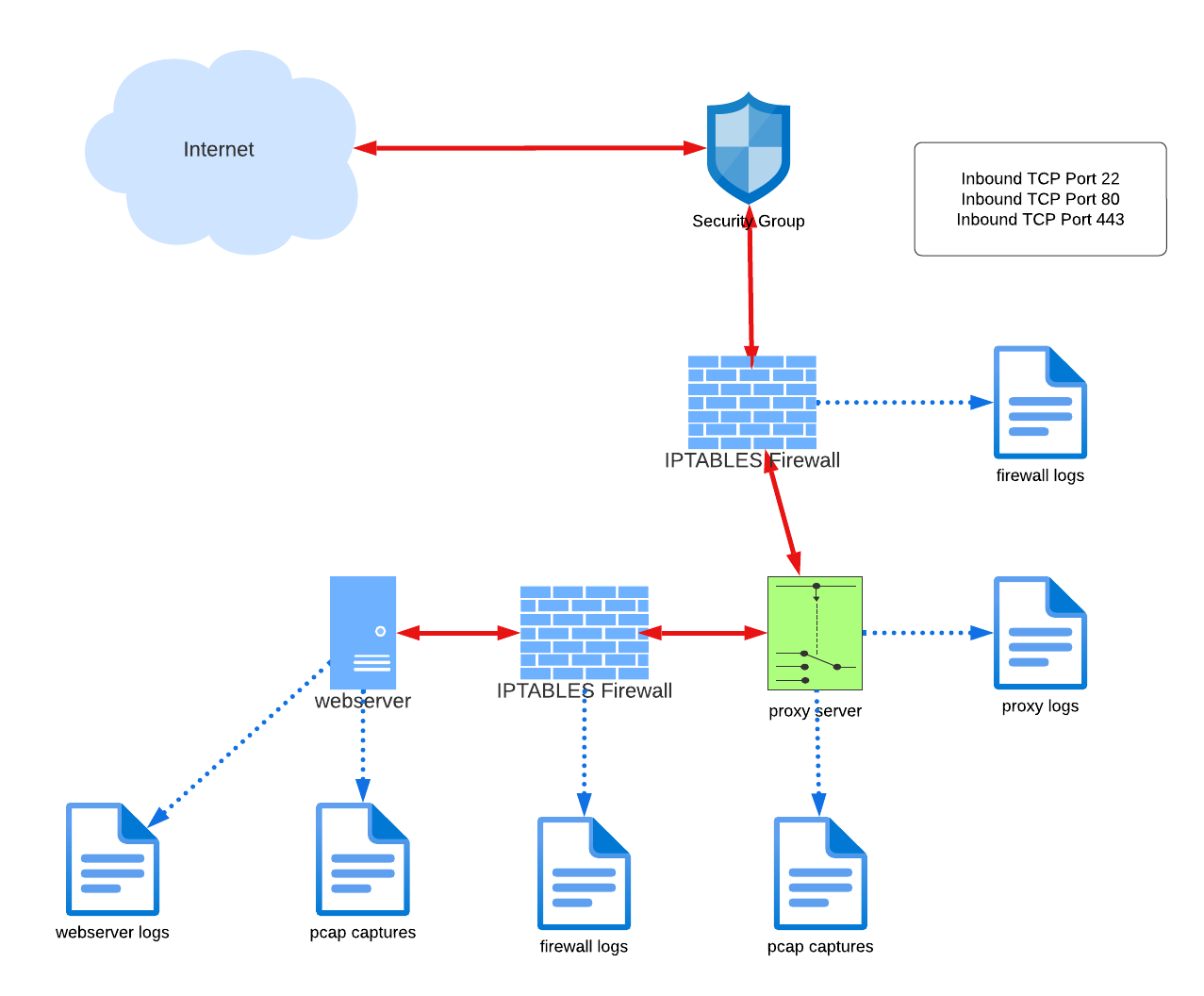
Location, Location, Location.
In the real estate business, it’s often said the three most important things are location, location, and location. The same can be said for where security practitioners opt to capture network packets for analysis. Today I’ll quickly examine the difference between a pair of deployments along with their strengths and weaknesses. I’m using a “import…
-

AWS Terraform Template
You want to get started in AWS and you want to learn how to do it with Terraform. You’ve read countless how-to articles, perhaps a book or two, and even watched some YouTube… and you still don’t feel like you “get it”. Or worse, you think you get it, but your code isn’t working. It’s…
-

Haystacks and Needles: Digging for Interest
While an intern with the ISC as part of the SANS.edu Bachelor’s Degree in Applied Cybersecurity (BACS) program, I performed a substantial amount of research and analysis on the daily. While most students install a honeypot locally on a Raspberry Pi to gather attack information, I took extra steps to deploy a personal global network of…
-

Migrating Virtual Machine VMware to Proxmox
With the recent announcement that VMware ESXi will no longer be made available for home users for free, many in the industry are turning to Proxmox for their virtual needs. Below find instructions I hastily cobbled together migrating a workstation today.
-

Two-Person Integrity
The two-person rule is a control mechanism designed to achieve a high level of security for especially critical material or operations. Under this rule, access and actions require the presence of two or more authorized people at all times. My first experience with TPI was as a Quartermaster in the United States Navy in the 90’s. The Figure…
-

Spyware in the Crosshairs?
The State Department is implementing a new policy today that will allow the imposition of visa restrictions on individuals involved in the misuse of commercial spyware. This new policy is the most recent action in the United States’ comprehensive approach to countering the misuse of commercial spyware. The governments of Australia, Canada, Costa Rica, Denmark,…
-

Cloudflare Penetration
For me, the story began back on November 2nd, 2023. For the better part of twelve hours, I either couldn’t login at all, or received errors when attempting to manage DNS records. I even opined:“Authentication Error: Code 10000”Please tell me this ain’t some Okta or similar sh*t. (https://twitter.com/TheDustinDecker/status/1720087581575217338) “The company says that this breach did…
-
Consumer Security Cameras
Know what you’re purchasing! Everyone is selling a flavor. The decision to add wireless security cameras to your home or business property is a wise one. The peace of mind associated with knowing a record of “what really happened” is available when necessary is a huge component of the value proposition most Americans base their…

