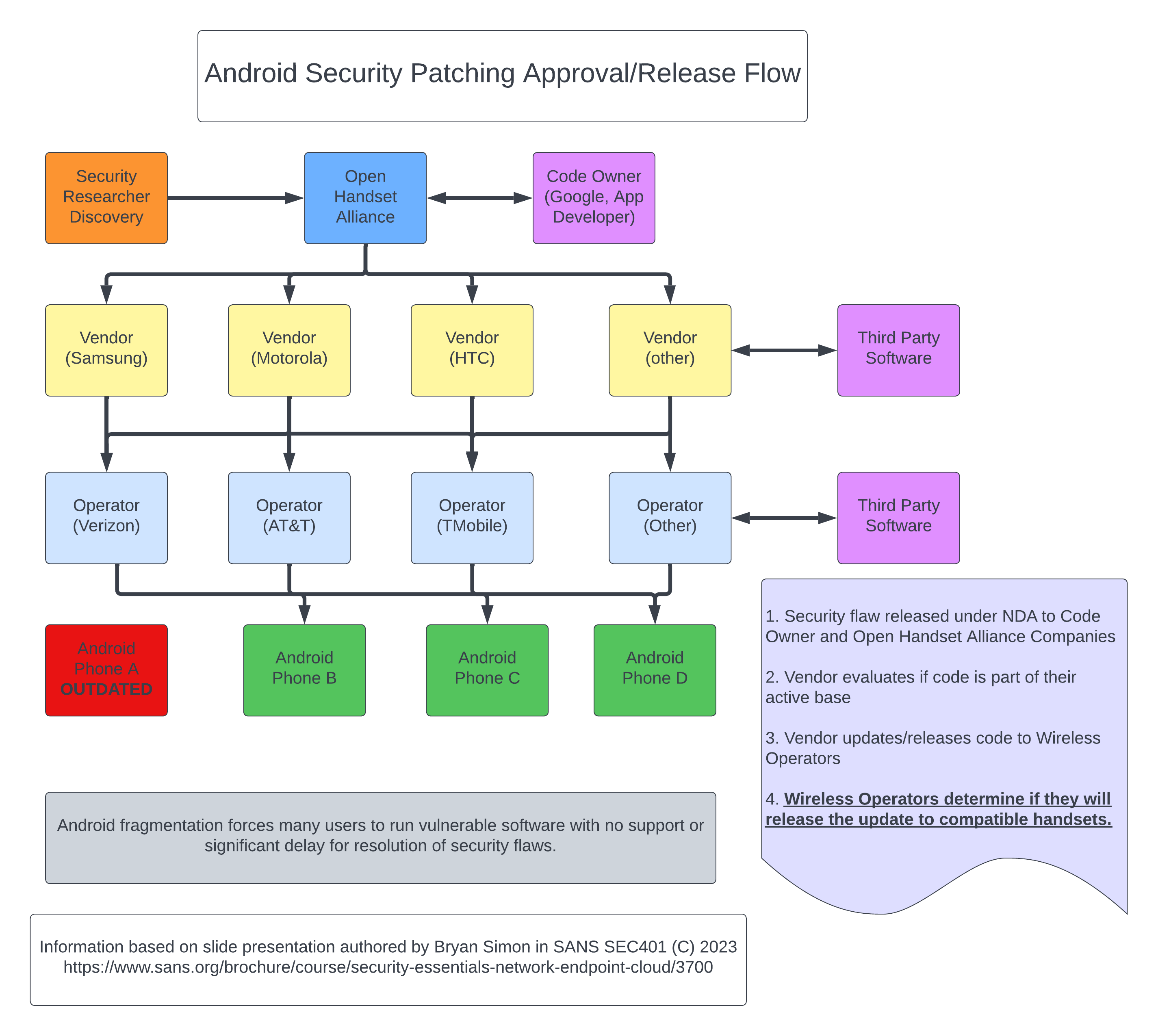
Tag: security
-

SANS SEC488
I’ve recently started the SANS SEC488 course, which is as intensive as all SANS courses tend to be. In the cloud a solid understanding of Identity and Access Management is crucial from the start; otherwise, there’s a high chance of making early mistakes in design and deployment that can cause significant issues later on. In…
-

Multi-OS Screen Blanking
The goal: Automate the binary application of daytime/nighttime screen timeout for Windows, macOS and Kali Linux.
-
Random Login Failures
A brief look at a very small sampling of failed logins. I’ve used green to highlight IP addresses known to be “OK” – Starlink out of Denver where my own connection terminates. Others are highlighted in dark pink and represent attacks with certainty. The orange highlighter is for other “items of interest”. Namely the use…
-

Think about building a “Go Bag”.
When the phone rings it’s important to have anticipated anything you may need and have it on hand – especially if you’re walking into an airgap. Here are a few I recently obtained that are performing exceptionally well for me. It’s also a good idea to have more than one, based on functional need. I…
-

Windows 11 Backup Strategy
Microsoft Windows 11 and Solid State storage solutions make it quite a bit easier to perform image-level backups of your computer. An image-level backup is a “kitchen sink, get everything” backup intended to allow you to restore your computer to the operating state it was in from a single image.
-

Cognitive Passwords – What Are They?
Another really simple analogy for these cognitive passwords is the classic “Safe Word”. Settle down now, I’m talking about that conversation you have with your children when they reach an appropriate age, wherein you agree upon a safe word or phrase that any stranger the child has never met must repeat if they are to…
-

Vehicle Controller Area Network Attacks
Vice is running an interesting article on Car Thieves Using Tech Disguised Inside Old Nokia Phones and Bluetooth Speakers. They detail the weaponization of theft with European hackers selling some twenty-dollars-worth of components in a unit for anywhere between a few hundred dollars to a few thousand. This allows folks with essentially no prior knowledge…
-

Replacing Passwords with Passphrases
Replacing passwords with passphrases is a good way to increase the security of your accounts, as passphrases are longer and more complex than typical passwords.
-

What is the best way to store passwords?
In our present context, “best” can represent pretty much any means that prevents accidental or intentional disclosure of a password.
-

What Is Two-Factor Authentication?
Two-factor authentication (2FA) is a security measure that adds an additional layer of protection to the traditional username and password login process.
-

Password Length vs. Complexity
In conclusion, while both length and complexity are important factors in password security, length is generally considered more important because it provides a stronger defense against brute-force attacks and is easier to remember.
-
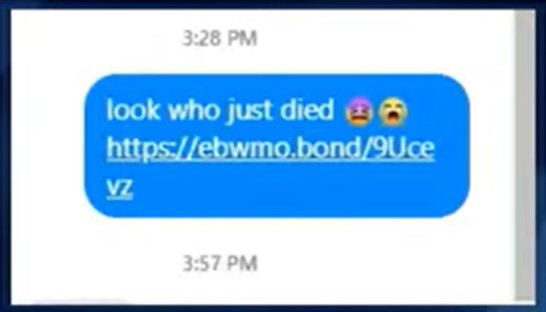
“Look Who Died” Phishing
In conclusion, “look who died” phishing is a dangerous form of cybercrime that preys on people’s emotions and curiosity. By staying alert and following the tips outlined above, you can protect yourself from these attacks and keep your personal information safe. Remember, if something seems too good to be true, it probably is.
-

What Is Phishing?
You might have heard of phishing and how terrible it can be to fall victim to it. But what actually is phishing? How does it work? Phishing stands as one of the most widely used cybercrime tactics right now. Phishing can be worryingly easy to carry out and can result in device infection and the…