-
You Are Safe! (Are You Sure?)
Bottom line, and I’m not necessarily bagging on Bitdefender, is that password protected files are skipped, and without regularly reviewing your logs, you may have no idea whatsoever they’re being skipped. Personally, my preference would be to immediately quarantine ANY password protected file encountered and require manual restoration. Trust – but VERIFY! Bitdefender is a…
-

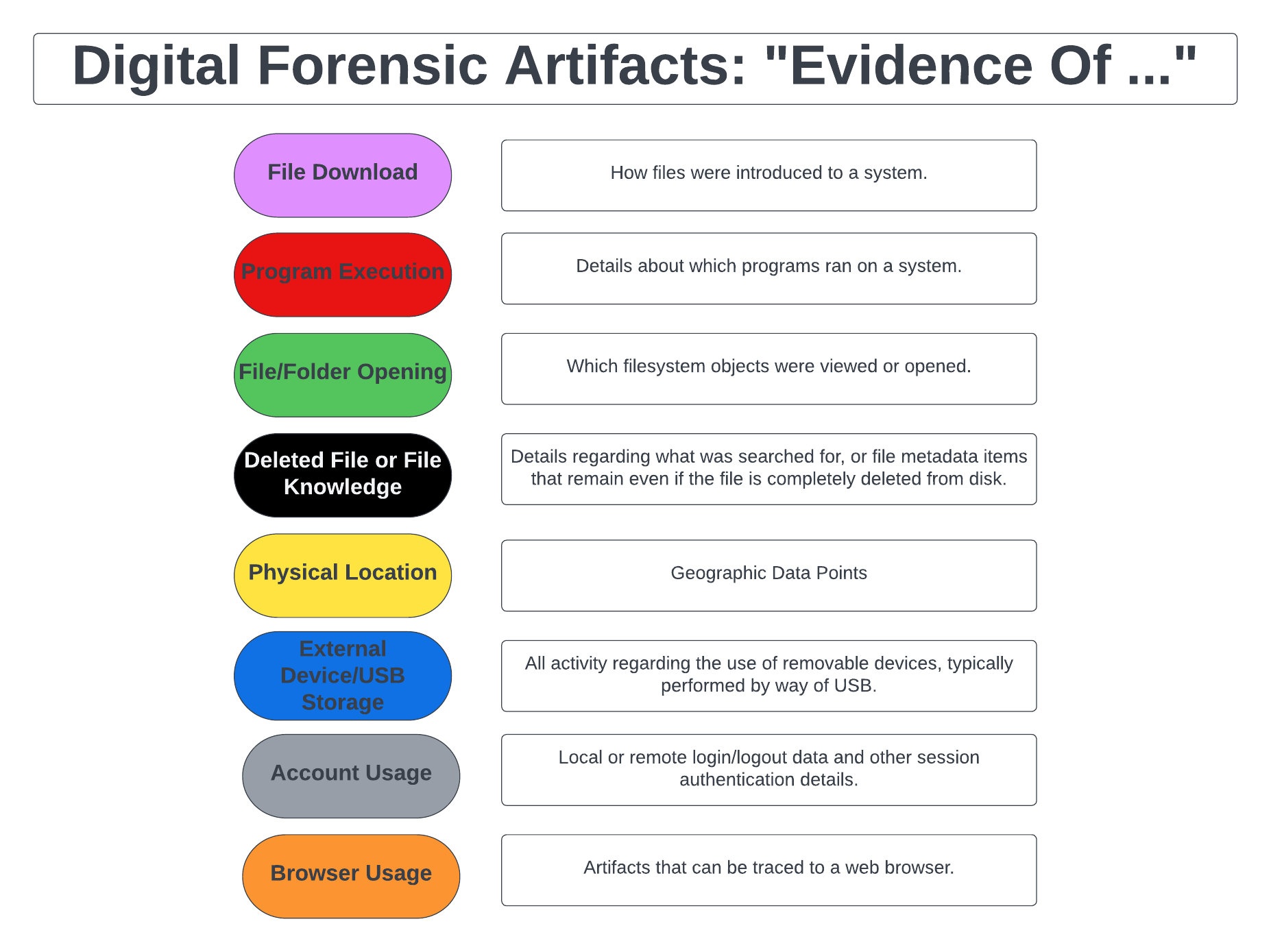
Vehicle Controller Area Network Attacks
Vice is running an interesting article on Car Thieves Using Tech Disguised Inside Old Nokia Phones and Bluetooth Speakers. They detail the weaponization of theft with European hackers selling some twenty-dollars-worth of components in a unit for anywhere between a few hundred dollars to a few thousand. This allows folks with essentially no prior knowledge…
-

Justice Dept. will investigate leak of classified Pentagon documents
This may take some time given the wide number of folks with access, but someone is probably going to jail over it:https://www.msn.com/en-us/news/us/justice-dept-will-investigate-leak-of-classified-pentagon-documents/ar-AA19BjV6
-

‘Find My iPhone’ app mistake causing angry residents to come to his house
https://abc13.com/richmond-news-find-my-iphone-app-apple-technology-mistake-lost-items-at-home/13085661/ This story very much reminds me of a prior geo-ip issue:https://www.theguardian.com/technology/2016/aug/09/maxmind-mapping-lawsuit-kansas-farm-ip-address
-

How thieves steal cars using network bus
It starts with a headlamp and fake smart speaker, and ends in an injection attack and a vanished motor. Read more: https://www.theregister.com/2023/04/06/can_injection_attack_car_theft
-

Replacing Passwords with Passphrases
Replacing passwords with passphrases is a good way to increase the security of your accounts, as passphrases are longer and more complex than typical passwords.
-

The Birthday Paradox
There are also certain forms of “randomness” created by computers that are far less random than you might expect – and their predictability makes cracking passwords easier as a result.
-

What is the best way to store passwords?
In our present context, “best” can represent pretty much any means that prevents accidental or intentional disclosure of a password.
-

What Is Two-Factor Authentication?
Two-factor authentication (2FA) is a security measure that adds an additional layer of protection to the traditional username and password login process.
-

Password Length vs. Complexity
In conclusion, while both length and complexity are important factors in password security, length is generally considered more important because it provides a stronger defense against brute-force attacks and is easier to remember.
-
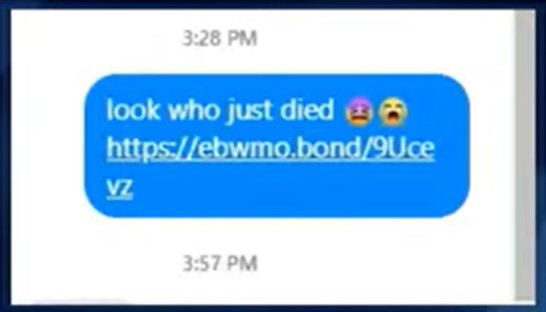
“Look Who Died” Phishing
In conclusion, “look who died” phishing is a dangerous form of cybercrime that preys on people’s emotions and curiosity. By staying alert and following the tips outlined above, you can protect yourself from these attacks and keep your personal information safe. Remember, if something seems too good to be true, it probably is.
-

What Is Phishing?
You might have heard of phishing and how terrible it can be to fall victim to it. But what actually is phishing? How does it work? Phishing stands as one of the most widely used cybercrime tactics right now. Phishing can be worryingly easy to carry out and can result in device infection and the…
-

Lesson One – The Human Element
The KISS Principle: KISS, an acronym for “Keep it simple, stupid!”, is a design principle noted by the U.S. Navy in 1960. First seen partly in American English by at least 1938, the KISS principle states that most systems work best if they are kept simple rather than made complicated; therefore, simplicity should be a…