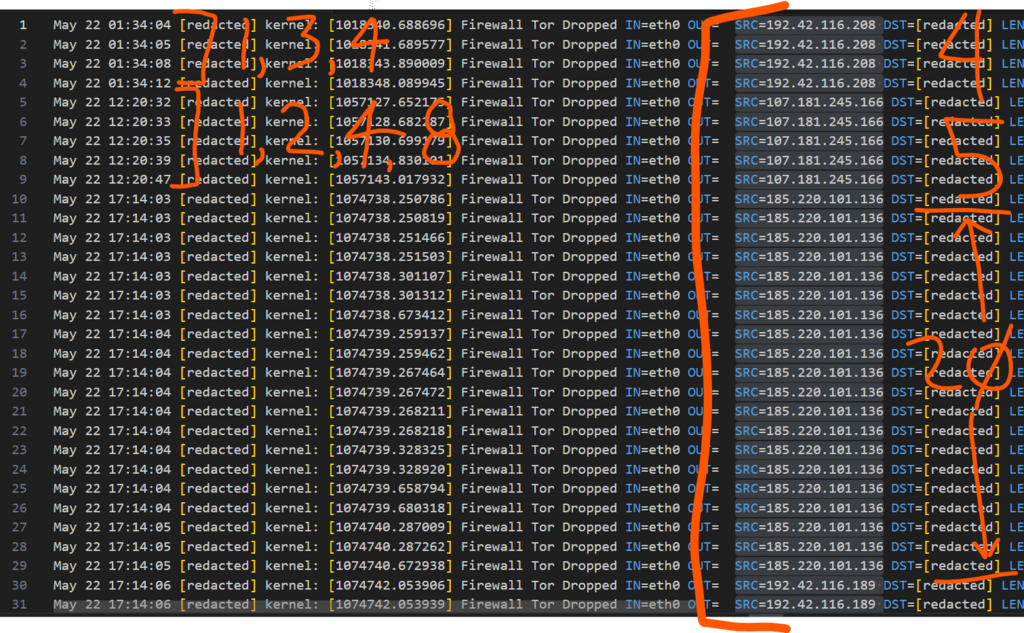
I’d love to say some days are slower than others but it’s not really true. I might spend an enormous amount of time, consuming new skillsets and sharpening my edge. While that’s going on, the Internet will of course continue to Internet. Let’s take a look at a three-day period of alert logging from a perimeter.
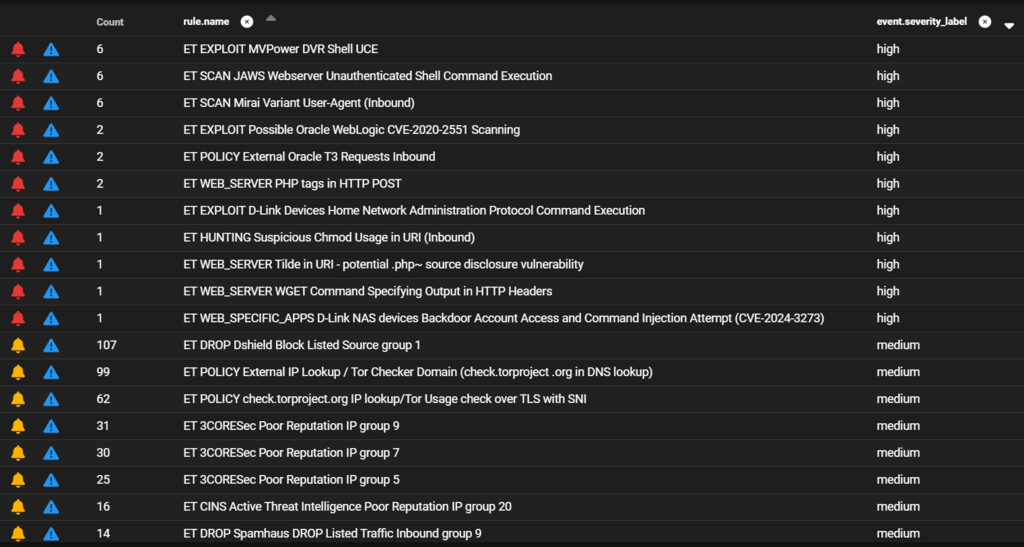
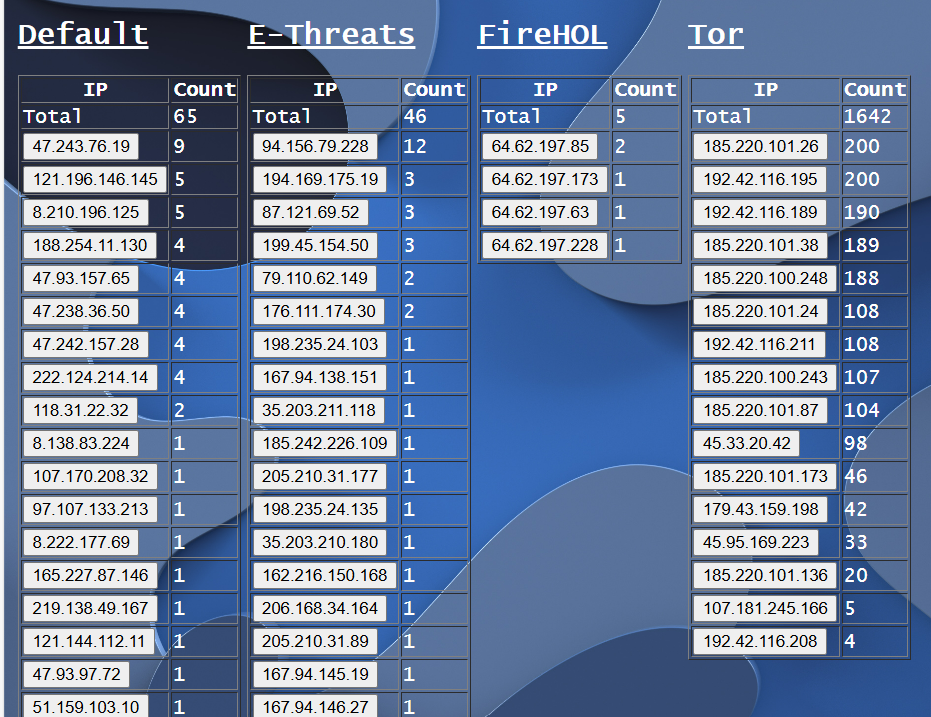
A custom firewall configuration utilizing Emerging Threats, FireHOL, and Tor lists for denying access at the perimeter.
“Default” captures remainder of denied packets.
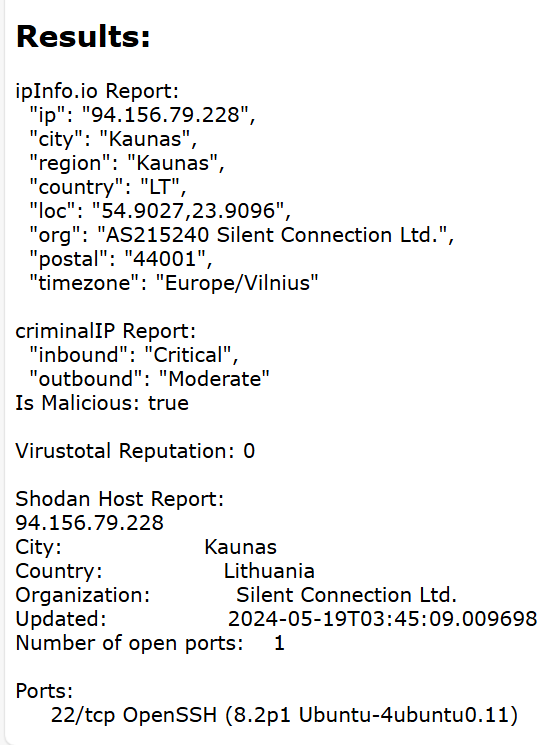
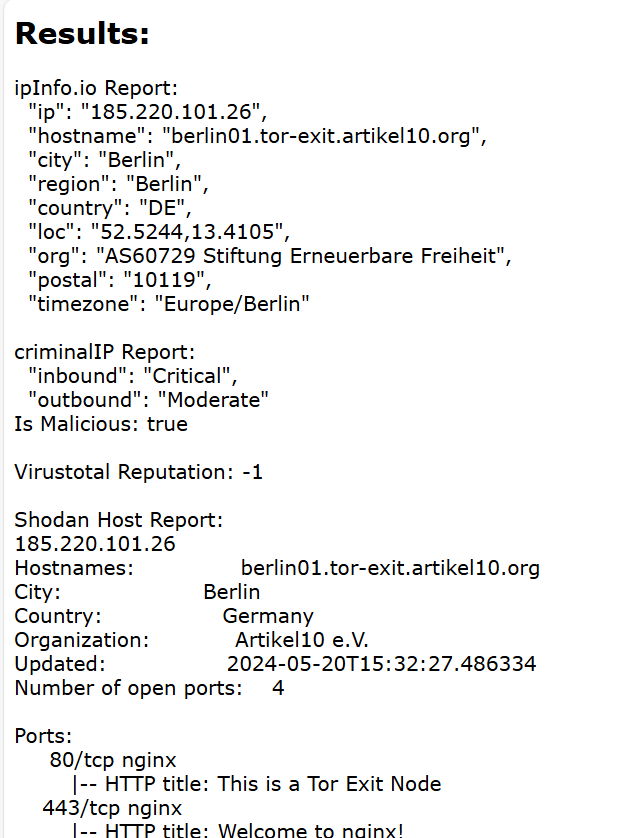
More of the standard “Noise” we expect from Asia and Europe, and even Tor. While the Tor traffic in and of itself isn’t particularly concerning, it’s interesting to note some of the behavior when packets are being dropped. The number of packets per exit node and time between them is somewhat revelatory. The log has a total of 1642 fresh entries, with a significant amount of repetition.
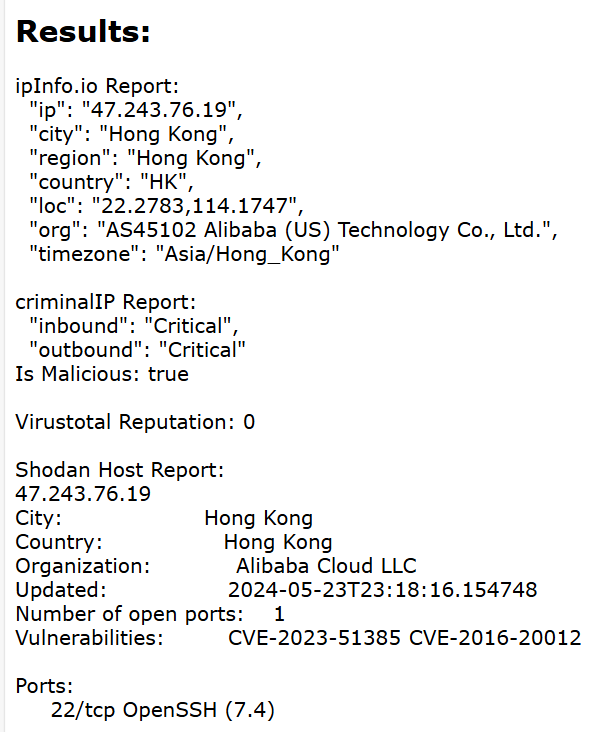
The geographical and network distance between source and destination, and subsequent TTL and latency, allow us to develop a picture fairly quickly.