 Bitdefender ™ Says “You are safe” Bitdefender ™ Says “You are safe” |  Bitdefender ™ Total Security also reports, “You Are Safe!” Bitdefender ™ Total Security also reports, “You Are Safe!” |
About a month ago I took a deep dive into my father’s laptop computer, an HP Notebook – 15-ay041wm (Touch) (ENERGY STAR), Circa April 2017, warranty expired 23 May 2019. This particular laptop shipped with Windows 7 and was later upgraded to Windows 8, and subsequently Windows 10.
Dad reported severely sluggish performance and occasional strange behaviors, although he often attributed this to being stuck with Viasat Satellite Internet services in their peaceful abode in the heart of the Ozarks. I spent a few minutes in his chair to take a look and it became immediately evident that something was woefully wrong with his computer. Simple tasks such as saving a .txt file, or any file for that matter, was being forbidden in a host of locations such as the My Documents folder, Desktop, and such. Failing a handful of other tests it became increasingly clear this machine was not a likely candidate for “cleaning” or “recovery”.
As an aside I’ll inject my own personal preference and opinion garnered from my years supporting Microsoft Windows in the trenches from MSDOS/WIN3.x to present day, and state that “upgrade” is a dirty word in the Microsoft world. I do my best to segregate personal data and operating systems, and when it’s time to move up to a major version release, I start with a brand-new installation of the new Windows release, then add my applications and personal data to that fresh installation.
Dad’s laptop shipped with a 1 TB 5400 rpm SATA (9.5 mm) hard drive. As luck would have it, I had a 1 TB SATA drive compatible with his unit with a slightly larger memory cache spinning at 7200 rpm. Armed with his jeweler’s screwdriver set, we cracked the unit open and performed an upgrade, stepped through the BIOS configuration, and then performed a fresh install of Windows 11. I then immediately added his laptop to my annual subscription of Bitdefender Total Security and bound the device to my Bitdefender Central console. This ensures that any fresh detections will notify me immediately, and I can also force updates remotely. Dad’s computer is humming along at a fair clip and it does “all the things” he needs. (I suspect were we to take an audit we would determine this is a relatively short list of things.)
So what should we do with this old hard drive? Wipe it and press it into service somewhere else? Maybe. I neglected to mention up front that with the exception of the now-defunct Windows Defender service, this laptop was running around on the Internet prophylactic-free for the better part of two years. The information security researcher in me presumed there MUST be some fairly nasty stuff lurking within, and I wasn’t disappointed. That’s NOT what this post is really about though. I’m here to discuss perception, common software statements, and configuration items that will say to you plainly, “You are safe”, when in fact nothing could be further from the truth.
I recently purchased a handy device that allows connecting 2.5/3.5 SATA HDD and 2.5/3.5 SSD units to my analysis station via USB3. I connected a multi-terabyte storage drive to my forensic station, mounted Dad’s hard drive as a read-only volume and took a forensic image with FTK Imager. I then performed a pair of aggressive scans of the image with a pair of commercial products; Malwarebytes and Bitdefender. I’m utilized licensed installations of these products vice the freeware versions.
Malwarebytes ran for just over nine and a half hours, and indicated a sole potential infection with a 97% confidence rating. There were no indications in the log file that any files had been skipped due to failure or other configuration issues. (So Malwarebytes isn’t completely off the hook – it identified one potential issue, quarantined nothing, and screamed right past the password protected files you’ll see in a minute.)
Objects Scanned: 441074
Threats Detected: 1
Threats Quarantined: 1
Time Elapsed: 9 hr, 34 min, 17 sec
File: 1
MachineLearning/Anomalous.97%, D:\PROGRAM FILES\WINDOWSAPPS\A278AB0D.MARCHOFEMPIRES_7.2.0.0_X86__H6ADKY7GBF63M\A278AB0D.MARCHOFEMPIRES.EXE, Quarantined, 0, 392687, 1.0.67791, , shuriken, , 2C5DA37E0194CA545C112061A405452B, 33EBE49468E418ADC05E207984FC7A861A0243199A26E85653B72B3B586D2086Bitdefender behavior was significantly different.
Upon completing a full manual scan of the volume, we’re told that no infections were detected.
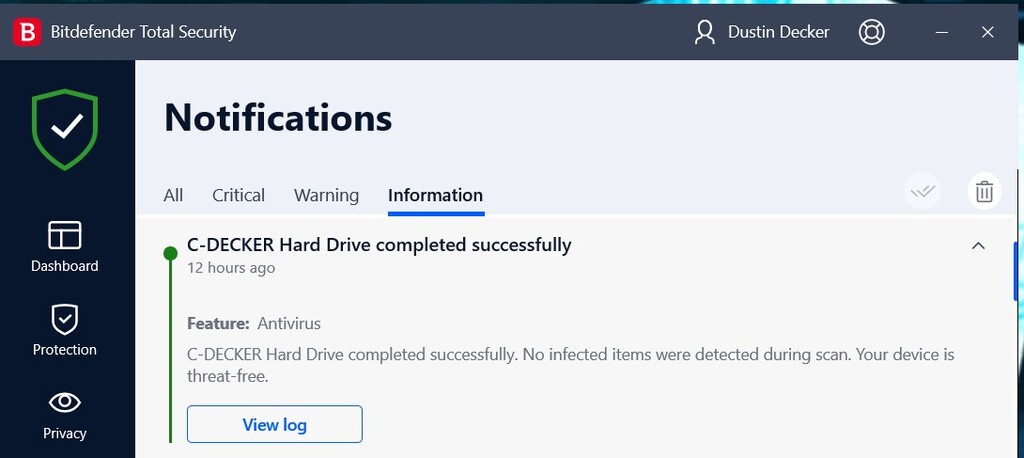
Viewing the log reveals a different story: True, no infections were found or reported, but we’ve skipped some files “because they’re password protected”. Hrm. Now why on Earth would my father need a password protected text file in the \ProgramData\SoundResearch path? (Answer: he doesn’t.)
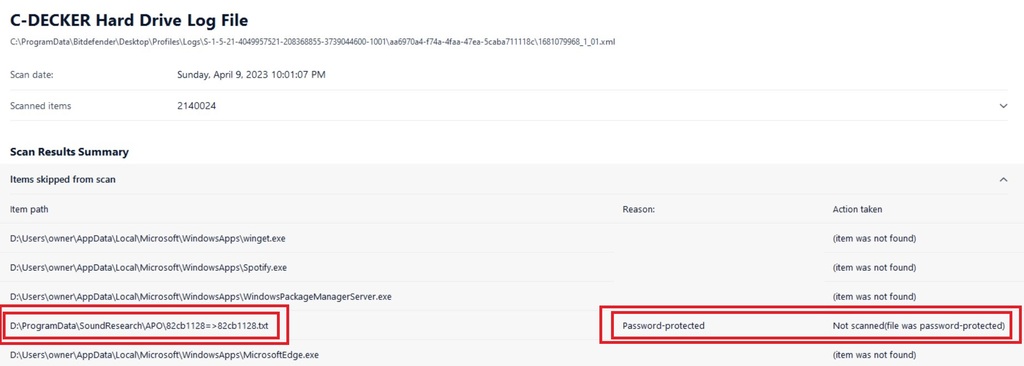
Why would my father need multiple copies of this password protected text file in multiple places?
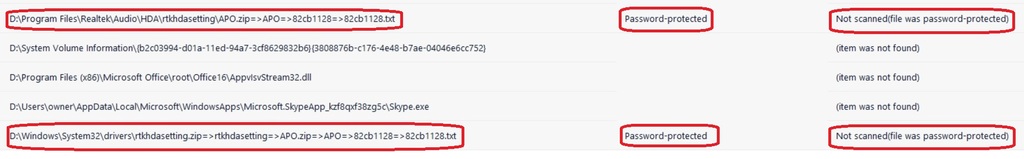
In the end, I performed a LOT of analysis on this drive image, and I expect to garner more mileage from it over time. To cut to the chase Dad had a particularly nasty Rootkit burrowed in deep. Remember that list of “things” my Dad does on the computer? One of those things is playing games – and it’s a relatively safe bet that downloading a trojaned copy of March of Empires was the initial threat vector.
But let’s back up for a moment. Let’s suppose that Bitdefender had been present and installed when he downloaded the game. Would it have been detected and stopped? That’s not necessarily the most binary yes/no of answers. I’ll need to spend some time in my lab to verify my suspicions. Here’s my hypothesis: The filesystem scanner would absolutely fail to detect this threat vector, but the Advanced Threat Defense module _might_ detect it if I attempt to access or unzip the contents of the file.
Bottom line, and I’m not necessarily bagging on Bitdefender, is that password protected files are skipped, and without regularly reviewing your logs, you may have no idea whatsoever they’re being skipped.
Personally, my preference would be to immediately quarantine ANY password protected file encountered and require manual restoration.
Trust – but VERIFY! Bitdefender is a PRODUCT. Opting to presume a password-protected file in a path we don’t expect (program files\etc.) is nefarious and quarantining by default, is a “process” based on a decision. The next question of course is, CAN I force Bitdefender to behave this way?

