“Evidence Of …”
Where to find goodies – and where the bodies are buried.
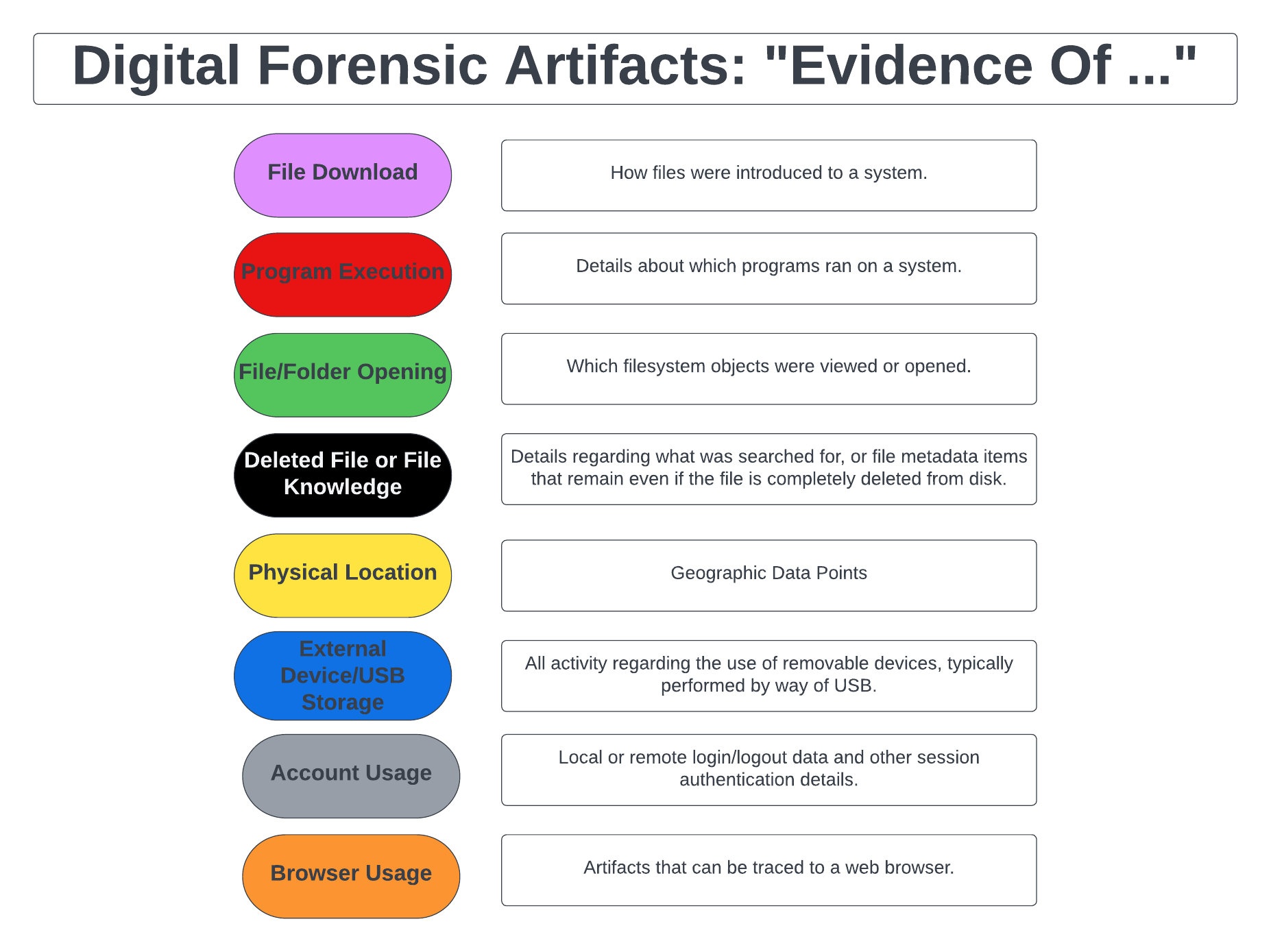
Digital forensic artifacts are pieces of information that can be gathered from electronic devices and computer systems during a digital forensic investigation. These artifacts can provide important evidence that can be used in legal cases, security investigations, or other types of digital analysis.
Some examples of digital forensic artifacts include:
- System logs: Logs that record system activity such as login attempts, network connections, and application usage.
- Registry entries: Entries that record information about the configuration and usage of software and hardware.
- File metadata: Data that describes the attributes of a file, such as its creation date, modification date, and access date.
- Internet history: Records of websites visited, search queries, and downloads.
- Email headers: Information that identifies the sender and receiver of an email, as well as the email’s path through various servers.
- Deleted files: Files that have been deleted from a device but can still be recovered through forensic analysis.
- Chat logs: Records of instant messaging or other chat conversations.
- GPS data: Location data collected by a device’s GPS receiver.
- Social media data: Information gathered from social media platforms, such as posts, comments, and likes.
- Malware: Evidence of malicious software, such as virus or Trojan horse, that may have infected a device.